Abstract
The
physical access control is actually the restriction of the access to the
physical space not the organization or business. The physical access control is
very valuable which can effectively let services to let the control, physical IT
assets as well as the buildings. In this research, the assessment of the physical
access control system is done to analyze and discover the weak point’s in the condominium.
Every company or service provider is working on making the defense system
stronger than before. For this purpose, there’s a need to find out major
weakness in the defense system. This research study is proving the most
important information on which weak points for condominium will be discovered
by the assessment of the access control.
TABLE OF
CONTENTS
ABSTRAK
i
TABLE OF CONTENTS
ii
LST OF TABLES iv
LST OF FGURES
v
LST OF ABBREVATONS
vi
CHAPTER 1 INTRODUCTON
1
1.1 Overvew
1
1.2 Problem
Background
1
1.3 Problem Statement
2
1.4 Research
Queston 3
1.5 Research
Objectves 3
1.6 Research
Hypothess 3
1.7 Scope of the study 4
1.8 Research Significance 4
1.9
Definitions of terms 4
1.10
Theoretical Framework
5
1.11 Theoretical Contribution 5
1.12 Summary 6
CHAPTER 2
2.1 ntroducton
7
2.2 Physical Access Control
8
2.3 Types of Physical Access control
8
2.3.1 Discretionary access
control (DAC)
9
2.3.2 Mandatory access control (MAC) 9
2.3.3 Role Based Access
Control (RBAC)
9
2.3.4 Attribute Based
Access Control (ABAC)
9
2.4 Archtecture of Access Control 10
2.5 Techncal Challenges Bometrc Applcatons’ Access
controls 11
2.6 Access
Control Archtecture 12
2.7 Physical
Access Control 13
2.8 Vulnerable or Weak ponts of an electronc lock
system 14
2.9 Development of Access Control Polces 16
2.10 Current Works on Access Control
17
2.11 Limitation 18
2.12 Research Gap
18
2.13 Related Works 18
2.14 Previous Researcher’s Significant Arguments. 19
2.15 Summary 21
CHAPTER 3
RESEARCH METHODOLOGY 22
3.1 Introducton
22
3.2 Research
Desgn
22
3.3 Operatonal
Framework
25
3.4 Framework evaluaton
Populaton
26
3.5 Data processng and
analyss
28
3.6 Summary
29
REFERENCES 30
LST OF TABLES
Table 2.2: Prevous Researchers Sgnfcant
Arguments 19
LST
OF FGURES
Figure 1.1:
Theoretical Framework
5
Figure 2.1:
Framework of Literature Review
7
Figure 2.2:
Architecture of Physical Access control system 10
Figure 2.3:
Architecture
14
Figure 2.4:
Authentication Systems
15
Figure 3.1:
convergent parallel design
23
Figure 3.2:
exploratory sequential design
23
Figure 3.2:
exploratory sequential design
24
Figure 3.4:
two-dimensional floor plan
26
Figure.3.5: Framework of spatial data model
27
LST
OF ABBREVIATIONS
|
PAC
DWP
|
-
-
|
Physical Access control
Discovering Weak Points
|
|
CPD
|
-
Convergent parallel Design
|
|
|
ESD -
|
|
|
|
|
|
|
Exploratory Sequential Design
Chapter
1
Introduction
1.1 Overview
The physical access control assessment study is showing the three are
different types of methods which are important in the identification of weak
points in the network used in a building. According to these methods, it is
discovering different traffic patterns and both of them came from physical and
logical standpoint tools. It is used for identifying different patterns and how
to find out different patterns (Douligeris & Mitrokotsa, 2004). This
research is also based on the physical access control assessment. Every
security system in the world has some limitations and every company wants to
provide services to its customers in effective way. The companies always focus
to provide services in smart way such as some building managements needs to
restrict services for specific apartment for some time. Some problem may also
exist the condominium which can badly affect the complete system. The physical
access control can also be very effective in the assessment, controlling and
monitoring the activities in the building’s network system to control or
identify the unauthorized access.
2 Background of the problem
1.2.1 In order to
identify and examine particaulr
background of the problem that is reaoted to the physical access control there
must be deep study on the said topic. Based
on intense interviews with condo owners and members of the condo industry in Ontario
and New York, and a detailed qualitative study of condo owners from Ontario, we
describe five overlaping and long-standing governance problems that threaten
and display more illusion than fact the notion of autonomy (Kansakar, 2019). This disjuncture is
not only due to traditional dilemmas of collective governance, but also to the
increasing impact on neo-liberal condominium by foreign and primarily
commercial interests (Chou & Suzuki, 2010).
1.2.2; An imortnat part of each and every security system
has been coprises by the access control systems nad it relevant devices. It
also includes even simplest single door systems and access control systems . It
also includes timer that can easily ensured the particular door can not stay
open. Access
control gadgets and frameworks contain a significant piece of each security
framework. Indeed, even the most straightforward single-entryway access control
framework incorporates in any event an electric strike to naturally open the
entryway, a clock to ensure that the entryway doesn't remain open throughout
the day, what's more, a ringer or light to demonstrate when the entryway is
opened or that it has not reclosed appropriately (Ballesteros,
2019).
In a huge scope security framework there might be interruption alerts,
leave cautions, shut circuit observation, watches and watches, actual
hindrances and gates, and an assortment of other gadgets and frameworks. The
consolidated preferences of these components establish a powerful actual
security framework. Different access control frameworks and gadgets are
currently accessible whose consolidated favorable circumstances establish a
powerful actual security framework. This article talks about these frameworks
and gadgets and helps the information security manager in deciding the
consumption needed to address the organization's degree of danger (Bowers, 2016).1.2.3 To
locate the frail focuses in both physical and Internet access control gadgets,
methods, programming frameworks, and section focuses, it can assist with
adopting the thought process of a mass aggressor, a criminal, an intruder, an
abusive behavior at home culprit wanting to hurt a particular worker, or a
cyberattacker (Albrecht, 2018).
Essentially watching representatives utilize the entrance control
focuses now and again of high traffic can highlight a few shortcomings,
chokepoints, or negative behavior patterns. Do all representatives utilize the
principle ways to the meeting room, or do they come in through uncontrolled
side passageways? Do workers permit unbadged representatives (or aliens) to
"back end" (Butler, 2007).1.2.4 . The
establishment of biometric sensors, for example, iris checking or unique mark
acknowledgment, can make even the most decided interloper vacillate while
attempting to access a protected spot. Actual access controls are components
that are intended to limit the danger of injury. A basic model is a solid match
on the entryway lock, which will debilitate numerous expected criminals. Now
and then everything necessary to determine the issue is an instrument to give
sufficient opportunity to contact the suitable specialists (Stolarski,
2020).
Simultaneously, we should recollect that the human factor can separate
nearly anything, even the most cleverly planned security framework.Shockingly,
in each organization there are individuals whom we trust, that may one day
imperil different workers. Workers' security ought to consistently be a
need. Likewise, research shows that the
most well-known sorts of assault are inside assaults, brought about by
disappointed, or even furious representatives (Bowers, 2016).
1.2.5 Actual
security controls, as different systems for guaranteeing organization and data
security, can be hard to execute. Guarding resources from all possible dangers
by all possible aggressors and methods for assault is unreasonable (Johnston
and Garcia, 2002). Supporting expenses and estimating execution is troublesome,
because of the trouble of distinguishing endeavors at assaults and relating
obstructed endeavors with explicit protections and possible harm. Security
also, uphold measures will in general be responsive in that framework
solidifying is normally attempted as a explicit reaction to a particular
security occurrence (Timbs, 2013) Current the
building is using the physical access control system but due to some reasons
some notable problems occurred in the internal system and residents had to face
many problems in condominium. Due to some internal unexpected problems, the
security became weaker because the system sometimes did not respond properly
and sometimes it gave permission to different people in the building.
Furthermore, the speed of the processing of the system was also very slow. In
this situation, it was very difficult for the management to handle the security
of the building. The problem was bigger and many people are also afraid of
these types of risks and threats. It has been observed by turning of the
numbers of research studies that are related access control but, there is not
any kinds of the particular study has been observed that can address the
keycard system for condominium particularly. No doubt, there are numbers of
blogs and various articles on the google can observed, but the specific
research has not conducted in order to address the solution of the keycard
system for condominium. While, there is not any particular study has been
observed on this topic, hence the current study is conducted to exploring
various aspects and particular features related to the keycards systems for
condominium. It also explores that why the keycard system is not effective and
why the electronic lock system is best suited and who had proposed this.
The keycard system is not considered as more effective because,
unluckily thus card can be stolen easily as well as it can be shared with
various other people even the group of peoples. By using this keycard system
there is risk of barcode as well as magnetic strip that is wearing away it also
becomes leaving the cardholder inaccessible until a replacement is sent.
Therefore, there are various other ways in order to enhance the security by
implementing two most important factors that are related to authentication that
would be required for the maintenance of the worker in order to utilize the
card reader. In any case, the person can forget their security codes and then
he required to fulfill the particular process for changing his password.
In simple words, the system is not effective and fail to ensure the
identity of the card wielder. It is the biggest problem in the building system
that can affect the users as well as the management of the company. By
considering the severity of the problem, the electronic lock system is the
suitable proposed solution which can effectively help in making system fast and
error free including enhanced security.
The electronic lock system is much better. Although, it has been
invented by the earliest accounts of biometrics that could be dated as far back
from the 500 BC in the Babylonian empire. The biometric identification system
was recorded first time in 1800s in the pacific region of Paris, France. It has
been developed by Alphonse Bertillon.
1.3 Problem statement
The problem statement for these thesis is that the physical access
control of building’s network infrastructure has some weak points, which makes
the security weaker. Due to this problem, sometimes it is difficult to restrict
services for some users in the building. The Current problem with the access
control system in the condominium is that keycard systems in the building are
problematic and most of them have at least one inherent weaknesses. In simple
words, the system is not effective and fail to ensure the identity of the card
wielder. It is the biggest problem in the building system that can affect the
users as well as the management of the company. By considering the severity of
the problem, the electronic lock system is the suitable proposed solution which
can effectively help in making system fast and error-free including enhanced
security.
1.4 Research Questions
Following are the research objectives (RO) for this study:
i.
What are the physical access control issues in the condominium?
ii.
How to analyze the physical access control issues in the condominium?
iii.
How to design guidelines for physical access control in the condominium?
iv.
What are the guidelines for physical access control in the condominium?
1.5 Research Objectives
The main objectives of the project are:
v.
To identify the physical access control issues in the condominium.
vi.
To analyze the physical access control issues in the condominium.
vii.
To design guidelines for physical access control in the condominium.
viii.
To evaluates the guidelines for physical access control in the
condominium.
1.6 Scope of the study
The current study particularly focuses on the access control for the
identification of weak points in the building network. The scope of the said
study is high because it explores the various authentic points that are related
to the security systems of the Bougainvilla Bukit Bintang. It participates for
controlling the difficulties of individuals to utilizing their privacy systems.
The current study is worthy because it covers the entire aspect related to
utilization key card systems, it also explores who the electronic lock system
is more effective than key card system. It explores the strategies in order
overcome various challenges that are occurs in the electronic lock system. The
scope of study is exactly elaborated the potential wroth of study, the said
study is worthy because it explains the numerous views related to effectively
assessing the physical access control for the identification of weak points in
the building network. This study will be worthy because it offers essential
information related to different types of gaps and the weaknesses in the
network for the condominium by conducting survey by using the self-structured
questionnaire
1.7 Research Significance
The said study is significantly contributing to the literature review???
by offering its essential points related to the cyber security and its relevant
aspects. It offers the news arguments related to the impact cyber security on
the defense system in the critical conditions. The current study is significant
for students and policy makers as well.
1.9 Theoretical Contribution
This study explores on the research supported assessment of physical
access control to get weak points for condominium and existing studying models
from various researchers are identified and investigated within the motivating
deployment to analyze the existing physical access control within the
condominium. Therefore, the design a proposed guidelines for physical access
control in the condominium. The current study is a worthy because it covers the
whole aspect related to utilization key card systems, it also explores who the
electronic lock system is more effective than key card system. Furthermore, the
evaluation and also the proposed conceptual model of discovering the weak point
within the condominium.
1.10 Theoretical Framework
Introduction
The below given thertaical frame owtk is illustratimg the relationship
among the variables that are particular require to explores the physical access
control along with its terminogies that are required to explaores that various
things. The need of physical access control has been explored un details by
explaining the theories iof several authors. The problem statement has been
exp;ained along with the back ground of the problem. Meanwhile in the below
given framework it is represented that utilization of key card systems and
utilization of the electronin lock sysem can be defined and exaplined for
maesurimg the physical access control system.
Physical access control sysyem is independent variables meanwhile
utilization of key card systems and utilization of the electronin lock sysem
are dependent variables.
Figure 1.1: Theoretical Framework //add more
not enough
1.11 Definitions of terms
// Rewrite something related to Phyiscal access control
Physical Access Control: it is the technique to control and monitor the
access or used to grant permission or restriction on the use of network
services. Physical access control is the restriction
of access to a physical space within the business or
organization. This type of access control limits access to
rooms, buildings and physical IT assets. In addition, physical
access control keeps track of who is coming and going in restricted areas.
1.12 Summary
Summing up all the discussion from above, it can be concluded that weak
point in the defense system can affect the building security. The study is
providing information related to the assessment of physical access control to
discover weak points. This chapter provides some hypothetical points, research
questions as well as the framework for this purpose. The current study is a
worthy because it covers the whole aspect related to utilization key card
systems, it also explores who the electronic lock system is more effective than
key card system.The current study is worthy because it covers the entire aspect
related to utilization key card systems, it also explores who the electronic
lock system is more effective than key card system. Therefore, there are various
other ways in order to enhance the security by implementing two most important
factors that are related to authentication that would be required for the
maintenance of the worker in order to utilize the card reader.
// You need to follow the sample chapter 2 and 3 get back to me if
you need any help with clear understanding not exactly to copyit as formatting and guideline .
Chapter
2
Literature
Review
2.1 Introduction
In this chapter, it is discussed about the relevant studies related to
physical access control and discovering the issues in the condominium. All of the related studies are linked with my
research based on the assessment of physical access control to discover weak
points. This chapter is providing a detailed discussion and critical analysis
of the ……………..
brief information and telling that what other researchers are saying on
this problems and what type of methods they applied to resolve this issue. The
summary of this chapter is presented in section 2.1 .Figure.2.1 below is the LR
framework: redo figure 2.1 don’t add cites
Types of physical
access control
|
Research 1
Physical access control
|
Research 3
Access control
architecture
|
Research 2
Technical challenges
biometric application’s access control
|
Research 4
Vulnerable or weak
points of an electronic lock system
|
Research Gaps and
limitations
|
Access control best
practice
|
Research 5
Development of access
control system
|
Figure 2.1: Framework of
Literature Review
2.2 Physical Access Control
Physical
access control may come in different forms, but the essential principle is to
establish obstacles such that unauthorized individuals do not penetrate a
physical area. In other words, the physical access control means that those
authorized to enter a location can only access it. Physical obstacles to entry
may be physical obstacles – an enclosed entrance, a twist, a barrier – or
obstacles to authority. An individual or sign that describes any constraints is
a barrier of authority. Consider a restaurant with an entry-level sign that
states that you only have workers outside of this location or that you will be
given a hospital receptionist on or outside visits. When talking about physical
access control, we apply mostly to the physical barrier scheme that operates in
accordance with authority barriers and authorization plans to enable sufficient
persons to enter and prohibit anybody else. Physical access control is at
the core of every successful defense scheme, and digital security is right up there.
While digital protection safeguards information, which obviously can be used to
destroy the credibility, finances or efficiency of a business or person,
physical security more viscerally protects individuals and equipment. The
coverage of a dangerous attacker who enters the office with an arm is full of
tragic consequences. Physical walls may stop unknown individuals coming into
server rooms or other places with unsafe materials and devices in less drastic
manner. A physical access control device mostly manages physical access, i.e.,
software and hardware, which is designed for combination with electronic door
locks and permit directives, in the modern age. These programs interpret the
rules for the company to check who has keys to whom (e.g. rooms, facilities,
vaults, etc.) locks and releases access. A catalogue of the multiple access
levels and lists of those access levels is given for such a system. It
regulates the locking mechanisms at different doors and barriers, according to
the person giving credentials' access level (Ballesteros, 2019).
2.3 Types of Physical Access control
Companies should differ from the form and sensitivity of data processed by
their access control system, says Wagner. The new model is known as the attribute-based
access control, and old access models include discretionary access control
(DAC) and mandatory access monitoring (MAC), Roll Based Access Control (RBAC),
the most popular model today (ABAC).
2.3.1
Discretionary access control (DAC)
The data owner
opts for control for DAC models. DAC is a way to allocate access rights based
on rules specified by users.
2.3.2
Mandatory access control (MAC)
MAC was
designed to use a nondiscretionary framework, in which individuals are given
access depending on a data clearance. MAC is a policy under which access rights
are allocated depending on legislation by a central authority.
2.3.3
Role Based Access Control (RBAC)
RBAC grants
access depending on a role of the user and incorporates core security
standards, such as “least privilege” and “separation of privilege.” Therefore,
anyone trying to access information can only access data that’s considered
appropriate for their role.
2.3.4 Attribute Based Access Control (ABAC)
ABAC assigns a
set of attributes to each resource and customer, explains Wagner. "To make
a decision on access to a source, this dynamic approach uses a comparative
evaluation of user attributes, including time of the day, position and
location." Organizations must determine which model is ideally tailored to
them based on data sensitivity and organisational data access criteria. In
particular, organisations that process personal identifying information (PII)
or other confidential information, such as the HIPAA or Managed Unclassified
Information (CUI) data, must have a central functionality of access control in
their security infrastructure, Wagner advises.
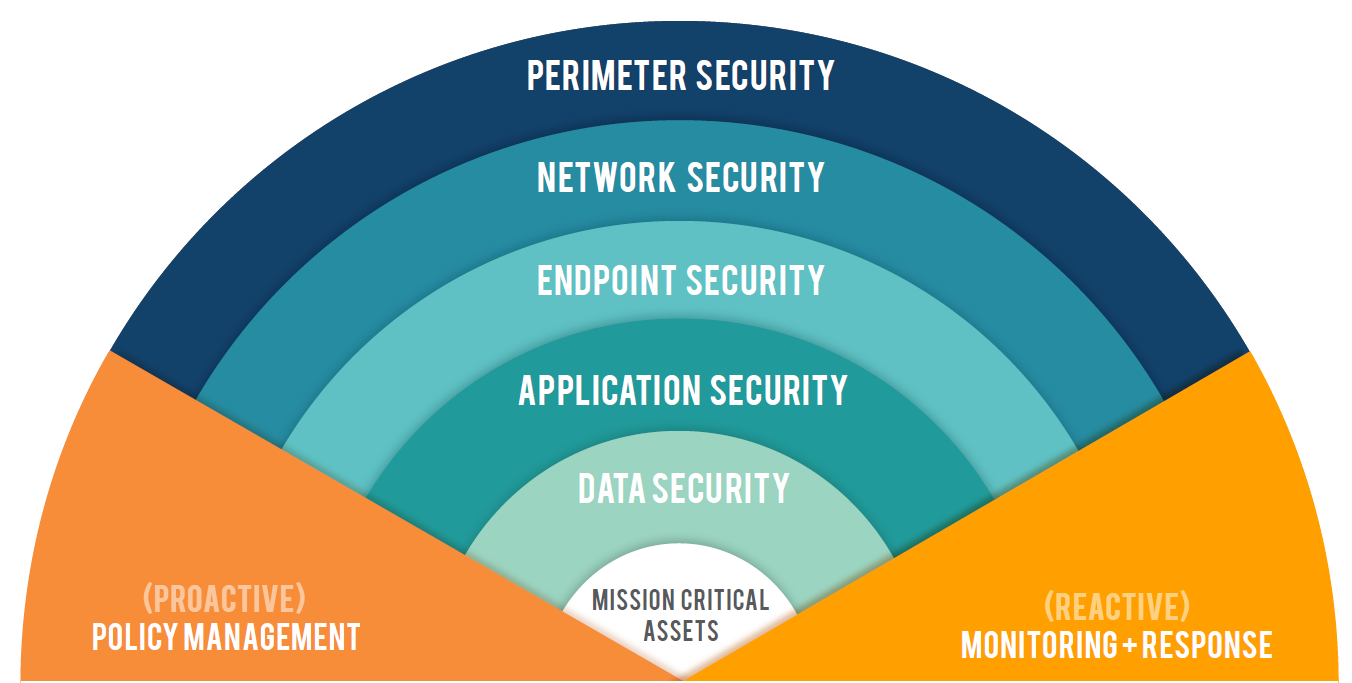
2.4 Architecture of Access Control
Most
organizations also required physical security including access control systems.
Enterprises big or small must secure their equipment, information and
employees. Following is a cursory look at what an elements, design and a
description of the components of a physical protection and access control
system entails (Alshehri & Sandhu, 2016).
Figure 2.2: Architecture
of Physical Access control system
Sofia (2017) desribed that we propose a systematic guide to data security in this article. To
safeguard the data of the enterprise properly, it is important to ensure that
all the data, both internally and externally, are obtained. Our methodology
consists of profiling the knowledge process participants, depending on what
data they use or process, how and when they use or process it. This helps the
company to recognize the faults and to take corrective action after the risk
evaluation, using sufficient security safeguards such as Data Leak Protection
(DLP) programmes designed to avoid data leak from inside to outside (Sofia, 2017).
Condominiums
are taken to be 'self-governing' societies with owners who jointly carry on
certain maintenance roles in the handling and maintaining of their buildings
and livelihoods in authorising laws, relevant legislation and statutory
amendments. Based on intense interviews with condo owners and members of the
condo industry in Ontario and New York, and a detailed qualitative study of
condo owners from Ontario, we describe five overlaping and long-standing
governance problems that threaten and display more illusion than fact the
notion of autonomy. This disjuncture is not only due to traditional dilemmas of
collective governance, but also to the increasing impact on neo-liberal condominium
by foreign and primarily commercial interests. We also look at recent
legislative attempts by Ontario and the State of New York and address
constitutional limits in solving these problems. We suspect that the condo
legislative amendment alone will solve condo housing issues and have solutions,
including going beyond condominiums' view of autonomous self-rule (Lippert & Treffers, 2019).
2.5 Physical
Access Control
Access Control is
a type of protection that restricts access to data or services for people in an
organisation. This is a critical element of every defence strategy. Pass
management authenticates and authorises individual workers to ensure a more
stable framework. Each successful access control scheme uses a mixture of
physical access control and logical access control. Regulation of physical
access requires limits on enterprise or company physical space. This method of
access management controls access to rooms, buildings and physical information
technology. Furthermore, the actual access system controls who is in restricted
zones. This will help to safe and protect your assets. Physical access controls
are not meant to block, but to regulate access. In other words, when access is
given and why access is granted, the data management administrator should know
who is given access. The functions, reliability and cost of physical access
control options are discussed in this article.
The
introduction of new immobilising goods in contemporary cities has been seen,
including gated and shut-down condominiums (CCs). The proliferation of these
urban goods has similar trends worldwide which are examined in this paper
according to five theoretical perspectives: geographical, economic, social,
political and cultural. These viewpoints cross some of the key topics relevant
to private residential growth for the discussion of current urban discourse.
These innovations tend to draw a growing number of social classes and have responded
to numerous planning systems. These innovations have arisen as CCs in Portugal
with a smaller scale and are studied in the Greater Oporto case report. The aim
of this paper is to present the Portuguese singularities of this phenomenon in
connection with the worldwide dimension. In our case study we see several
significant particularities closely correlated with the Portuguese planning
system. Any of these elements have a detrimental influence on the urban
landscape around it. As a result, CCs need clear planning strategies to resolve
the detrimental effects in local social and urban fabrics they are supposed to
produce. Without these measures, CCs are expected to lead more to a more
fractured urban environment, along with other private residential projects (Cruz & Pinho, 2009).
2.6 Technical Challenges Biometric Applications’ Access controls
Mumtazah, Ahmad, & Adnan (2012) described that the latest innovations in biometric
technology along with growing risks to information security have proliferated
the use of biometrics to protect information and support networks,
infrastructures and processes. This paper addresses the technological issues
and challenges of biometric technology in physical and conceptual information
management access control systems. The topic concerns device efficiency in
terms of robustness and the identification potential of various biometric characteristics
for the real operating environment. It also advertises multiple safety risks,
including spoong and replay assaults. This paper further highlights
interoperability problems and criteria for accurate testing and monitoring. The
ultimate conversations offer imperative perspectives into the usefulness of
information- security and decision making trade-off and risk assessment
analyses (Mumtazah, Ahmad, & Adnan, 2012).
Sampemane, Naldurg, & Campbell (2002) also told that the
active spaces, together with
supporting facilities, are physical spaces enhanced by heterogeneous storage
and networking devices. This integration encourages user communication and
enables a greater degree of user-device interaction. For multiple types of
programmes, an active area may be configured at various times. We present an
access management scheme that automates access control policy development and
implementation for a number of Active Space setups. Our framework expressly
recognises the numerous forms of collaboration between user groups and the
reliance on physical and virtual dimensions of protection in Active Spaces. Our
paradigm supports both voluntary and obligatory access management measures and
uses role-based access control mechanisms to handle users and permissions
effectively. Based on context details, we dynamically allocate permissions to
user functions. We illustrate how complex domains can be generated using an
example scenario. This enables managers and software creators to configure
access management strategies on a need-to protective basis. We also have a
semiformal overview and study of our model and demonstrate how through complex
shift in access control permissions, we retain security properties. We also
prove that our paradigm protects the least fortunate concept, encourages
obligation differentiation and avoids expanded freedom (Sampemane, Naldurg, & Campbell, Access control for Active Spaces. ,
2002).
2.7 Access Control Architecture
A
user authentication process is one of the prerequisites for access protection.
A customer will be recognized and given a certificate in our system through a
validation service. This credential follows any service request submitted by a
user (or an application made on behalf of a user) in the room and is used to
recognise the requester by the Access Control Service. This paper does not
depend on the unique authentication mechanisms; we will use any authentication
method, which safely transfers the credentials to the user so that they cannot
be distorted, hacked or forged. Provided these properties, the framework for
access control may depend on the request identification credentials. We believe
that only permitted users have physical access to the room. Usually, users are
expected to swipe access cards in an electronic door block to allow them to be
entered1. Of course, this system is open to users who sneak with other
legitimate users, but once a user reaches the room without a valid certificate,
he or she cannot access services. Other users can also identify intruders in
the room, and this is a helpful function. The Active Space knows who the
consumers in an environment are and configures protection policy for this
knowledge (Sampemane, Naldurg, & Campbell, Access control for Active Spaces. ,
2002).
Figure 2.3: Architecture // redesign your own
Ratha, Connell, & Bolle (2001) explained that due to the fact that biometric
authentication provides many benefits over other authentication techniques; the
use of biometrics for user authentication has grown considerably in recent
years. Particularly in unattended remote applications such as ecommerce, it is
necessary for such biometrics based authentication systems to withstand attacks
when used in security-critical applications. In this article we illustrate the
intrinsic benefits of biometric authentication, describe the weak links in
biometric authentication schemes, and propose new ways to eliminate some of
these weak links. While fingerprint identification is used in the whole process
for example purposes, our study includes other biometric methods (Ratha, Connell, & Bolle, Enhancing security and
privacy in biometrics-based authentication systems., 2001).
2.8 Vulnerable or Weak points of an electronic lock system
In the context
of a pattern recognition system, a standardised electronic lock system may be
casted. Figures display the steps of such a generic method. The first stage
includes the acquisition of biometric signal by the customer (e.g., the inkless
fingerprint scan). The signal produced generally differs considerably from
submission to presentation; pure pixel-based matching techniques therefore do
not work consistently. This is why the second stage of signal processing seeks
to make this simple input signal more invariant (e.g., in terms of fingerprint
minutiae). The invariant representation also depends on the basic biometrical
characteristic of a spatial domain or transforming (frequency) domain
characteristics. An invariant prototype is stored in the database representing
the person during inscription in a biometric authentication method. The
required template is extracted and matched with the template from the newly
obtained input signal to authenticate the user against a specific ID. The match
comes to a conclusion that takes into account geometry, lighting and other
acquisition factors, depending on the closeness of these two models. Please
notice that in this context even password-based authentication schemes can be
specified. The keyboard is the interface for input. You will display the password encrypted as the extractor and the comparator as
the player. The prototype database refers to the encrypted database of the
password (Ratha, Connell, & Bolle, Enhancing security and privacy in
biometrics-based authentication systems., 2001).
Figure 2.4: Authentication
Systems // redesign your own
A
great deal of study on inside prevention is detected. Though recent work in
this field is encouraging, our analyses of technologist in financial,
healthcare and other market contexts show a split between what
"real-world" practicers want and what the research and vendors
communities can deliver. We're looking at the protection of attacks using
access control. We present the theoretical principles of current access
management, examine the demands of today's effective technologies for
enterprise environments and provide a survey of actual infrastructure that
meets those criteria, on the basis of our arguments in this ethnographic study,
which targets both technology and human market systems that push it and
constrain it. This paper finishes by discussing places that provide a specific
hope for the war to deter insider attacks for potential advances in access
security (Sinclair & Smith, 2005).
As
described by Ye, Heidemann, & Estrin
(2004) that the article suggests S-MAC, a protocol developed for wireless
sensor networks, which is a medium access control (MAC). Wireless sensor
networks are using computers and sensing equipment powered by batteries. For a
collaborative application such as environmental control, a network of these instruments
may cooperate. We plan to deploy sensor networks ad hoc; nodes remain
relatively inactive for long stretches, but become triggered when anything has
been observed unexpectedly. The MAC is distinct from standard wireless MACs,
like IEEE 802.11, in many respects because of these sensor network properties
and applications: energy efficiency and self-configuration are primary targets,
while equity and latency are not as relevant per node. S-MAC employs many
innovative strategies to decrease energy consumption and help self-settings. It
requires low-duty cycle functioning in a multichip network. Nodes form virtual
clusters, which are based on traditional sleep patterns and minimise overhead
controls. In order to prevent overhearing of unwanted transport, S-MAC uses
in-channel signalling. Finally, for programmes that require in-network data
processing, S-MAC uses the message pass. The paper presents S-MAC efficiency
measurement findings for a sample sensor node, UC Berkeley Mote, and exposes
fundamental energy, latency and power output compromises. S-MAC has been
demonstrated, as compared with 802.11-like sleepless MAC, to gain substantial
energy savings (Ye, Heidemann, & Estrin, 2004).
2.9 Development
of Access Control Policies
In order to
guide 'best practice' practices within an organization's IT security system it
is important to define the main access control (IT) information management
policies. It underlines the important change away from clustered mainframes to
dispersed networked computer systems by explaining the importance of security
access management policy in the IT security programme. The study revealed that
the conventional and proven methods of security management employed in the
mainframe setting do not extend to distributed applications, thereby defining a
certain amount of intrinsic threats using emerging technologies. In order to
provide effective risk management measures, access control policy on IT
Structures should be provided, considering the sensitive existence of
information assets of organisations. The changing infrastructure has made
centralised security technologies difficult to handle distributed network
networks. This study found that corporate governance and risk management
techniques involved legislation to monitor the access to an Information System
to secure an organization's information assets. The paper presents a high-level
guide to the application of security policies through ISIs, management
responsibility policy and other simple access security policies for individual
systems and distributed systems. Keywords: Access management, IT policy,
applications spread, security rules, policies for access control (Ward & Smith, 2012).
2.10 Current Works on Access Control
The Internet of
Things (IoT) prevalence enables heterogeneous embedded intelligent systems to
deliver smart services in collaboration with or without human interference. IoT
also poses questions about safety and protection as it leverages large-scale
IoT-based technologies such as Smart Gird or Smart Cities. The authorization of
access is essential for resource sharing and preservation of information among
the top security issues facing IoT. The central permission server, which can be
a performance bottleneck or a single point of failure, is one of the
shortcomings of today's access management (AC). BlendCAC, a decentralised,
capabilities-based AC for the defence of IoTs, is introduced in this article.
The Blende CAC aims at powerful access controls in large-scale IoT systems for
computers, resources and information. A capability delegation mechanism for
access authorization propagation is proposed on the basis of the blockchain
network. A comprehensive identity-based capability token management approach is
suggested, which takes advantage of a smart contract for registration,
dissemination and revocation of the access authorization. In the proposed
BlendCAC system, IoT machines are their own master to manage their resources
instead of being controlled by a centralised authority. The experimental
findings introduced and evaluated on the Raspberry Pi device and a local
private blockchain network show the efficacy of the BlendCAC proposal to
include a decentral, scalable, lightweight and fine-grained IoT framework AC
solution (Xu, Chen, Blasch, & Chen, 2018).
2.11 Limitation
The
establishment of the access control system is to work for the security of the
associations. The increased concern of the resident is towards the property
damage and to elevate the incident of the security program. Some of the major
limitations of the research are listed below,
·
The
complete evaluation of the facilities is not considered for the qualified
security consultant.
·
The vital assets are linked to the security
system.
·
The staff is supposed to ensure employees
management of the systems.
2.12 Research
Gap
The research
project is focused on covering the identified research gap. The research gap is
identified after reviewing existing research literature including books and
research articles published in creditable research journals. Previous research
studies have focused on the access control system. Researchers have studied
pass management and physical access control methodologies. While research
papers are also published on several important issues and challenges of
biometric-based access control systems. Additionally, research papers have also
provided detail on access control architecture and weaknesses of the electronic
lock system. However, in these research studies, researchers have not paid
attention to weak points specifically in the physical access control system and
its assessment process. Thus, identified research gap for this research project
is required to be covered by our research project.
// add Identified Factors + Table
2.13
Related works
Sofia (2017)
desribed that we propose a systematic guide to data security in this article.
To safeguard the data of the enterprise properly, it is important to ensure
that all the data, both internally and externally, are obtained. Our
methodology consists of profiling the knowledge process participants, depending
on what data they use or process, how and when they use or process it. This
helps the company to recognize the faults and to take corrective action after
the risk evaluation, using sufficient security safeguards such as Data Leak
Protection (DLP) programmes designed to avoid data leak from inside to outside
(Sofia, 2017).Condominiums are taken to be 'self-governing' societies with
owners who jointly carry on certain maintenance roles in the handling and
maintaining of their buildings and livelihoods in authorising laws, relevant
legislation and statutory amendments. Based on intense interviews with condo
owners and members of the condo industry in Ontario and New York, and a
detailed qualitative study of condo owners from Ontario, we describe five
overlaping and long-standing governance problems that threaten and display more
illusion than fact the notion of autonomy. This disjuncture is not only due to
traditional dilemmas of collective governance, but also to the increasing
impact on neo-liberal condominium by foreign and primarily commercial
interests. We also look at recent legislative attempts by Ontario and the State
of New York and address constitutional limits in solving these problems. We
suspect that the condo legislative amendment alone will solve condo housing
issues and have solutions, including going beyond condominiums' view of
autonomous self-rule
(Lippert & Treffers, 2019).
2.14 Table: Previous
Researcher’s Significant Arguments.
|
No
|
Author / Year / Country
|
Field of Study / Research
|
Base Theory
|
Proposed Model / Framework Perspective & Factor
|
Findings & Contribution
|
|
1.
|
(Ratha, Connell, & Bolle, 2015)
|
This is a
literature review based study focused on enhancing security and privacy
systems
|
Comparing different security and privacy systems that uses
electronic lock systems for validations
|
1) Unattended
remote applications
2) Bio-metric
based authentications
3)Fingerprint authentications
|
Research find
that electronic lock system have some weaknesses which need to eliminate by
improved for its useful application in the security system of organizations.
|
|
2.
3.
|
(Sampemane, Naldurg, & Campbell, 2017)
Sofia &
New York
(2017)
|
This is a
literature review based study focused on enhancing security and privacy
systems
This article,
To safeguard the data of the enterprise properly, it is important to ensure
that all the data, both internally and externally, are obtained.
|
Access
control system can be used for active spaces and software infrastructure.
Our methodology consists of profiling the knowledge process
participants, depending on what data they use or process, how and when they
use or process it.
|
1) Group Modes
2) Common mode
3) Collaborative Mode
4) Individual Mode of access to the
Active Spaces
Data Security
2). Systematic
3). Data Leak Protection
|
Research concluded that novel models and architectures require virtual
access and integration for semi-formal models and changes access control
modes based on interactive behavior
Research Conducted it this
helps the company to recognize the faults and to take corrective action after
the risk evaluation, using sufficient security safeguards such as Data Leak
Protection (DLP) programmes designed to avoid data leak from inside to
outside
|
2.15 Summary
This chapter
explained some portion of the past related works applicable to the
comprehension of the issue with a specific end goal to accumulate data, which
further upgrade my comprehension furthermore gives far-reaching rules toward
accomplishing the targets of my task. This chapter will outline the relevant
theory and researches which are going to be applied and therefore, the topic
has covered during this section including research Gap, Previous Researcher’s
Significant Arguments and ted to the physical access control and discovering
the weak points additionally, some figure will help to understand the physical
access control within the condominium. The next chapter is going to discuss the
Research Methodology of this study. // Rewite clear summary add more
Chapter 3
Research Methodology
3.1 Introduction
This chapter is providing the
important information related to physical access control to find the weak
points in condominium. The proposed operational framework for the physical
access control is authorization framework. A crucial factor in ensuring vital
infrastructure such as airports, harbors, transport hub, power plants and
military assets is physical access control. A conventional large-scale project
can cover multiple locations with numerous multi-story structures with special
security measures that can house several fields. Moreover, different routes of
linking areas may be accessible. The fact that standard pathways such as
corridors, stairways and lifts are possible or there can be indirect paths,
such as the roof, partition walls and ventilation ducts, makes manual access
management especially difficult for the physical access control system, as well
as spatial and communication connections between managed spaces. Specifically,
it is hard to comprehend the three dimensional existence of the world by
two-dimensional floor plans, which are widely used by managers for physical
access control configuration and management.
3.2 Research
design
The research design for this project
is consist of two method. The combination of mixed mode methods is used for analysis
and interpretations of data. The research data is containing qualitative data
sets and quantitative data sets. Firstly, an exploratory sequential design is
used for the research findings of qualitative and quantitative research data
sets. See the following model representing this method or design.
Figure 3.1: convergent
parallel design
Under this
model, quantitative and qualitative data set is compared and analyzed for
relevancy. Then, based on analysis results are determined and interpretations
are discussed in the research project. Another research design used in this
project is convergent parallel design. See the following diagram.
Figure 3.2: exploratory
sequential design
In
this model are discussed which will be use qualitative data to explore
quantitative findings. This kind of study illustrates the use of mixed methods
to explain qualitatively how the quantitative mechanisms might work.
Quantitative Data Collection (Survey/Questionnaire)
|
Quantitative Data Analysis
|
Connecting Quantitative and Qualitative Phase
|
Qualitative Data Collection
|
Qualitative Data Analysis
|
Integrating the Quantitative and
Qualitative Results
|
Figure 3.3:
exploratory sequential design
3.3 Operational
Framework
In this article, we propose a new
tool to promote security control of physical infrastructure, which uses
Building Knowledge Models (BIM). In recent years, the use of BIMs has been
increasingly appropriate in the construction, engineering and building sectors.
BIMs have a shared archive of organized three-dimensional data on physical
structures, spatial connections, and dynamical construction processes. The
method to model building details starts from the building's design stage and
progresses over the lifecycle of the building, collecting a large range of
static and operating data. The use of BIM in an authorization tool will make
the method more straightforward when observing buildings in three dimensions
and requires spatial relation analysis to be used in the access control
process. In the following parts, we introduce an example situation to explain
challenges of therapy science. We are considering how an administrator offers
physical access for various stakeholders within an airport environment. A
member agency within the airport could be an airport employee. However, they
must manage their access to communal spaces and systems through a single access
policy. In the airport's hair-ding baggage area marked by X in Figure, an
emergency fix is required. At most, airports, a contracting firm would have
pre-approved technicians to carry out this mission. The ideal method should
start from there to carry out a job not as a challenge for individual resources
or doors in a physical access control scheme. A collection of services that can
be accessed based on operating requirements and the general physical security
strategy of the facility should be determined using the authorization
framework. For example, accompanying repair contractors might claim only that
they should have access to doors fixed with a CCTV camera surveillance. For
unique services that conform to machine policies, it is not feasible to provide
pre-defined access patterns. For example, it is possible to predefine a route
for cleaners, which can be extended to all users of that class, to enter a
specific space in the installation.
Figure 3.4:
two-dimensional floor plan
3.4 Framework evaluation Population
In our research into use of BIMs for
access management in large-scale buildings, we present an access control
administration tool. The implementation of this prototype solves the three key
issues we found early: intuitive implementation of physical access control
procedures, simple maintenance of physical access control schemes, and
efficient auditing of physical access control records. The essence of this
management tool lies in the principles of the building knowledge model that we
discussed earlier in our authorization system. In three main steps of access
regulation, the authorization process uses BIMs: policy formulation,
administration of the policies and decision-making. As shown in below Figure
each procedure is gathered in the authorization system by a specific component.
In the following paragraph, we give a short summary of this system. The BIM
layer is composed of a model server loaded with BIMs. These BIM files come from
various stakeholders of the facility migrated on the model server to a BIM. The
Spatial Modification Module offers the requisite spatial functions for the
licensing framework. This involves various spatial functions such as
positioning access doors in a room, evaluating accessibility based on a
specified beginning and stopping point, or listing services within a specified
space. The simulation engine produces 3D and 2D models of BIM data for various
authorization frame processes such as space justification and policy
transformation. This background adopts a structured XACML architecture as its
authorization layer. The authorization model embraces a convergent physical and
functional approach to access management. The authorization model this paper
focuses only on our proposed tool for physical access control administration.
The BIM layer provides the framework to apply the spatial data model in order
to replicate resources and calculate spatial functions. We have incorporated as
part of this prototype visualization, spatial logic, and political change. The
access knowledge interface lets these modules interface with an actual physical
access control device, but it does not form part of the current tool version.
The essence of this management tool lies in the principles of the building
knowledge model that we discussed earlier in our authorization system. In three
main steps of access regulation, the authorization process uses BIMs: policy
formulation, administration of the policies and decision-making. As shown in
Figure 2 each procedure is gathered in the authorization system by a specific
component. In the following paragraph, we give a short summary of this system.
Figure.3.5:
Framework of spatial data
model
3.5 Data
processing and analysis
The challenge
in disclosing the existing rights of access for a user or function is one of
the key challenges with current access control management instruments. Although
text lists of user/role rights may belong to them, administrators can have
difficulties in matching the privileges to the spacing of a facility. The
prototype allows administrators to interpret the rights of a user or function
as open spaces to meet this necessity.
Access
Management Policy Check: Administrators can conduct numerous policy searches;
optimize users' search results, duties, requirements etc. Search results. The
method can also be used to edit policy guidelines.
Find Access
Control Policy: Administrators can scan for a policy and can refine the
findings through users, positions, requirements, etc. Check Access control
policy. The tool can also edit those policy laws.
Technology
managers should load and visualise the places they can navigate current access
management policies for individual users or functions. This search element can
be further minimised by additional criteria and timescales for scenario
preparation and analysis. Another fascinating functionality is the use of BIMs
to represent connections between objects where research on the access rights
can be carried out and contradictions can be found at the political level.
3.6 Summary
A conventional
large-scale project can cover multiple locations with numerous multi-story
structures with special security measures that can house several fields.
Moreover, different routes of linking areas may be accessible. The method to
model building details starts from the building's design stage and progresses
over the lifecycle of the building, collecting a large range of static and
operating data. The essence of this management tool lies in the principles of
the building knowledge model that we discussed earlier in our authorization
system. The challenge in disclosing the existing rights of access for a user or
function is one of the key challenges with current access control management
instruments.
References
[1]
Alneyadi, S., Sithirasenan, E., & Muthukkumarasamy, V. (2016). A
Survey on Data Leakage Prevention Systems. Journal of Network and Computer
Applications, 62. doi:10.1016/j.jnca.2016.01.008
[2] Alshehri, A., & Sandhu, R. (2016).
Access control models for cloud-enabled internet of things: A proposed
architecture and research agenda. . In 2016 IEEE 2nd International
Conference on Collaboration and Internet Computing (CIC)In 2016 IEEE 2nd
International Conference on Collaboration and Internet Computing (CIC),
530-538.
[3]
Ballesteros, M. (2019). U.S. Patent No. 10,194,318. Washington, . DC: U.S.
Patent and Trademark Office.
[4]
Chou, B. H., & Suzuki, E. (2010). Discovering community-oriented roles of
nodes in a social network. In International Conference on Data Warehousing
and Knowledge Discovery, 52-64.
[5]
Cruz, S. S., & Pinho, P. (2009). Closed Condominiums as Urban Fragments
of the Contemporary City. European Planning Studies, 1685–1710.
[6]
Ding, Y., Peddinti, S. T., & Ross, K. W. (2014). Stalking beijing from
timbuktu: a generic measurement approach for exploiting location-based social
discovery. . In Proceedings of the 4th ACM Workshop on Security and Privacy
in Smartphones & Mobile Devices , 75-80.
[7]
Douligeris, C., & Mitrokotsa, A. (2004). DDoS attacks and defense
mechanisms: classification and state-of-the-art. Computer Networks,
643–666.
[8]
Lippert, R. K., & Treffers, S. R. (2019). Condominium self-governance?
Issues, external interests, and the limits of statutory reform. self-governanc,
1025-1049.
[9]
Mumtazah, S., Ahmad, S., & Adnan, W. (2012). TECHNICAL ISSUES AND
CHALLENGES OF BIOMETRIC APPLICATIONS AS ACCESS CONTROL TOOLS OF INFORMATION
SECURITY. Computer Technologies .
[10]
Ratha, N. K., Connell, J. H., & Bolle, R. M. (2001). Enhancing security
and privacy in biometrics-based authentication systems. IBM Systems
Journal,, 614–634.
[11]
Sampemane, G., Naldurg, P., & Campbell, R. H. (2002). Access control for
Active Spaces. . 18th Annual Computer Security Applications Conference, .
[12]
Sinclair, S., & Smith, S. W. (2005). Preventative Directions For Insider
Threat Mitigation Via Access Control. . Advances in Information Security, ,
165–194.
[13]
Sofia, B. (2017). Holistic Approach to Data Protection - Identifying the Weak
Points in the Organization. International Conference on Big Data,
Knowledge and Control Systems Engineering.
[14]
Wang, Y., Xie, W., Yu, X., & Shark, L.-K. (2015). An automatic physical
access control system based on hand vein biometric identification. IEEE
Transactions on Consumer Electronics, 61(3), 320-327.
[15]
Ward, P., & Smith, C. L. (2012). The Development of Access Control
Policies for Information Technology Systems. Computers & Security,
356–371.
[16]
Xu, R., Chen, Y., Blasch, E., & Chen, G. (2018). Blendcac: A
blockchain-enabled decentralized capability-based access control for iots. In
2018 IEEE International Conference on Internet of Things (iThings) and IEEE
Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and
Social Computing (CPSCom) and IEEE Smart Data (SmartData), 1027-1034.
[17]
Yanushkevich, S. N., Shmerko, V. P., Boulanov, O., & Stoica, A. (2010).
Biometrics Theory, Methods, and Applications. In S. N. Yanushkevich, V. P.
Shmerko, O. Boulanov, & A. Stoica, Decision-making support in
biometric-based physical access control systems: Design concept architecture
and applications. (pp. 599-631). IEEE Press .
[18]
Ye, W., Heidemann, J., & Estrin, D. (2004). Medium Access Control With
Coordinated Adaptive Sleeping for Wireless Sensor Networks. IEEE/ACM
Transactions on Networking,, 493–506.
[19]
https://pcmh.ahrq.gov/sites/default/files/attachments/MixedMethods_032513comp.pdf



